Authors:
Victor van der Veen (Vrije Universiteit Amsterdam), Yanick Fratantonio, Martina Lindorfer (UC Santa Barbara), Daniel Gruss, Clementine Maurice (TU Graz), Giovanni Vigna (UC Santa Barbara), Herbert Bos, Kaveh Razavi and Cristiano Giuffrida (Vrije Universiteit Amsterdam)
Journal/Conference:
In Proceeding of the 23rd ACM Conference on Computer and Communications Security
Source:
https://dl.acm.org/doi/10.1145/2976749.2978406
Abstract
Recent work shows that the Rowhammer hardware bug can be used to craft powerful attacks and completely subvert a system. However, existing efforts either describe probabilistic (and thus unreliable) attacks or rely on special (and often unavailable) memory management features to place victim objects in vulnerable physical memory locations. Moreover, prior work only targets x86 and researchers have openly wondered whether Rowhammer attacks on other architectures, such as ARM, are even possible. We show that deterministic Rowhammer attacks are feasible on commodity mobile platforms and that they cannot be mitigated by current defenses. Rather than assuming special memory management features, our attack, DRAMMER, solely relies on the predictable memory reuse patterns of standard physical memory allocators. We implement DRAMMER on Android/ARM, demonstrating the practicability of our attack, but also discuss a generalization of our approach to other Linux-based platforms. Furthermore, we show that traditional x86-based Rowhammer exploitation techniques no longer work on mobile platforms and address the resulting challenges towards practical mobile Rowhammer attacks. To support our claims, we present the first Rowhammer-based Android root exploit relying on no software vulnerability, and requiring no user permissions. In addition, we present an analysis of several popular smartphones and find that many of them are susceptible to our DRAMMER attack. We conclude by discussing potential mitigation strategies and urging our community to address the concrete threat of faulty DRAM chips in widespread commodity platforms.
RowHammer
In this paper, A generic technique for deterministic Rowhammer exploitation is suggested using commodity features offered by modern OSs. Authors show the feasibility on mobile platforms (Android and ARM)
Rowhammer is one of hardware bugs using Software-induced hardware fault that affects DRAM chips by solely performing read operations. To exploit the Rowhammer bug, three primitives are required: (1) fast uncached memory access, (2) physical memory massaging to trick victim component to use a memory cell that is subject to the Rowhammer bug, (3) physical memory addressing which is crucial to perform double-sided Rowhammer.
Related works
Previous researches show techniques to exploit rowhammer bug on X86 architecture.
- for fast uncached memory access bypassing CPU cache:
- Explicit cache flush using ‘clflush’ instruction. The clflush can be called in unprivileged mode.
- Cache eviction sets repeatedly accessing addresses that belong to the same cache eviction sets. This is useful when ‘clflush’ is not available (ex, javascript)
- Non-temporal access instructions to write directly accessing memory (memset or memcopy).
- For physical memory massaging, three approaches are proposed as follows:
- Page table spraying with expectation for some of PTEs to be probabilistically landed in vulnerable physical memory pages which attacker intends.
- Memory deduplication by mapping two virtual pages on same physical page
- MMU paravirtualization which is only available in Xen MMU paravirtualized VM.
- Physical memory addressing is crucial to perform double-sided rowhammer. Following two techniques are available on x86 architecture:
- Pagemap interface file has complete info about V2P mapping and can be access in unprivileged mode.
- Huge pages are backed by physically contiguous physical pages.
All these things cannot be applied to Android and ARM for various reason (i.e. non-deterministic, hardware-specific, special memory management features, non-default feature, etc.). In addition, there is no memory layout specification and there is no swap space on Android and ARM. Moreover, OS may kill high-memory pressure process. In these reasons, other approaches are required to exploit rowhammer bug on Android and ARM.
Drammer
The authors introduce Drammer. Firstly, for the mobile devices, no specification about row-size exists. So they use timing-based side channel to find out the exact row-size of memory using the observation that the time for accessing tow memory pages from same bank is longer than that from different bank. Secondly, userland accessible DMA buffer is exploited for both uncached memory access and physical memory addressing which is required to perform double-sided rowhammer. Finally, phys feng shui is proposed for physical memory massaging by exploiting the buddy allocator into reusing and partitioning memory in a predictable way.

Before conducting phys feng shui, flappable bits should be searched. Once a bit is flipped, it can be easily flipped again later. The list of flipped bits is name as template. Then, whole process of phys feng shui is conducted as follows:
- (step1) All available physically contiguous chunks of size L are first exhausted (i.e. allocate until no longer possible.
- (step2) Probe them for vulnerable templates for later exploitation. then all chunks of size M are exhausted, leaving the allocator in a state where blocks of size M and larger are no longer available.
- (step3) Release L chunks having vulnerable bits.
- (step4) Allocated M chunks again in the previously released memory
- (step5) Release vulnerable M chunks and all L chunks to avoid going out-of-memory later.
- (step6) Allocate S chunks until first allocated in the vulnerable M chuck.
- (step7) Insert paddings until the vulnerable chuck.
- (step8) Finally map the vulnerable PTE.
After successful memory massaging, double-sided rowhammer can be performed to flip a bit in the PTE. Then, root privilege can be acquired in a way that different physical pages are repeatedly mapped into the vulnerable chuck to scan kernel memory for the security context of own process (struct cred). If the context is found, root privileges can be acquired easily by overwriting uid and gid.
Evaluation
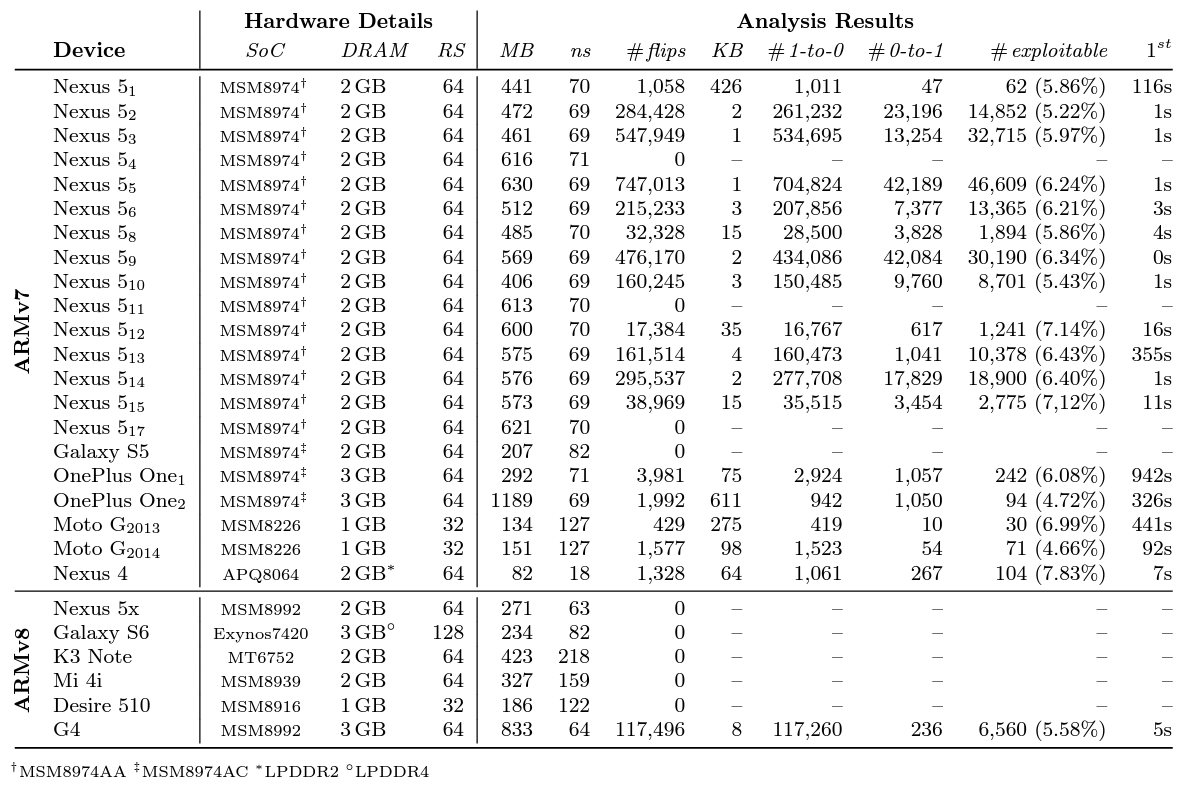
The proposed method was evaluated with 23 of ARMv7 smart phones and 6 of ARMv8 smart phones. Bit flips are found on 20 out of 29 tested devices. It also shows that ARM memory controllers are fast enough to do rowhammer and LPDDR is vulnerable. The first bit flip occurred within 16s on 11 devices while it took up to 942s on the other devices. However, after the first exploitable flip, exploitation takes at most 22 seconds only.
Discussion
This paper presents the first technique to perform deterministic rowhammer exploitation using only commodity features and evaluate the effectiveness of their implementation on multiple android devices. Moreover, the authors suggest possible mitigations for future security (i.e. restriction of userland interface, memory isolation and integrity, memory exhaustion prevention, etc.)
I think further researches can be conducted. (1) In this paper, the evaluations are conducted only on linux-based OSs. It would better if more study progress about IOS-based OS. (2) The authors consider only the kind of DRAM of devices. This study can be further if various states of the DRAM are considered (i.e. manufacturer, lifecycle, the level of wearing out, temperature, etc.)
'CS > Operating System' 카테고리의 다른 글
| [논문 리뷰] IPLFS: Log-Structured File System without Garbage Collection (0) | 2023.05.21 |
|---|---|
| [논문 리뷰] SoftTRR: Protect Page Tables against Rowhammer Attacks using Software-only Target Row Refresh (0) | 2023.05.20 |
| [전공생이 설명하는 OS] 메모리 관리 - (2) Virtual Memory (0) | 2022.06.02 |
| [전공생이 설명하는 OS] 메모리 관리 - (1) Partition/Page/Segment (0) | 2022.06.02 |
| [전공생이 설명하는 OS] 동기화 - (6) 식사하는 철학자 문제 (코드 포함) (0) | 2022.05.31 |
![[논문 리뷰] Drammer: Deterministic Rowhammer Attacks on Mobile Platforms](https://img1.daumcdn.net/thumb/R750x0/?scode=mtistory2&fname=https%3A%2F%2Fblog.kakaocdn.net%2Fdna%2FpdNZj%2FbtsgyL7Lytj%2FAAAAAAAAAAAAAAAAAAAAAGvmMPsBZ3zyHtliJTE6yh7_K61kt_82xweeqwN6l-yi%2Fimg.png%3Fcredential%3DyqXZFxpELC7KVnFOS48ylbz2pIh7yKj8%26expires%3D1772290799%26allow_ip%3D%26allow_referer%3D%26signature%3Db8AKTLYhl2q1x0nYNrPfNUWhJqQ%253D)