Authors:
Yoochan Lee and Jinhan Kwak, Seoul National University; Junesoo Kang and Yuseok Jeon, UNIST; Byoungyoung Lee, Seoul National University
Journal/Conference:
USENIX security '23 (open access)
Source:
https://www.usenix.org/conference/usenixsecurity23/presentation/lee
Abstract
The stealthiness of an attack is the most vital consideration for an attacker to reach their goals without being detected. Therefore, attackers put in a great deal of effort to increase the success rate of attacks in order not to expose information on the attacker and attack attempts resulting from failures. Exploitation of the kernel, which is a prime target for the attacker, usually takes advantage of heap-based vulnerabilities, and these exploits' success rates fortunately remain low (e.g., 56.1% on average) due to the operating principle of the default Linux kernel heap allocator, SLUB.
This paper presents Pspray, a timing side-channel attack-based exploitation technique that significantly increases the success probability of exploitation. According to our evaluation, with 10 real-world vulnerabilities, Pspray significantly improves the success rate of all those vulnerabilities (e.g., from 56.1% to 97.92% on average). To prevent this exploitation technique from being abused by the attacker, we further introduce a new defense mechanism to mitigate the threat of Pspray. After applying mitigation, the overall success rate of Pspray becomes similar to that from before using Pspray with negligible performance overhead (0.25%) and memory overhead (0.52%).
Motivation
The Linux kernel is a major attack target to accomplish the attacker’s objectives. For attackers, the stealthiness of an attack is one of the most important requirements when launching the exploitation. Focusing on the popular heap-based kernel vulnerabilities, it is difficult for attackers to assure the successful exploitation. This is because the attacker should be able to roughly predict the current allocation status. However, it is nearly impossible for the following two reasons: (1) the kernel’s object allocation status is not accessible by attackers, (2) the kernels’ memory allocator shows non-deterministic, pseudo-random behavior, rendering it difficult to infer its internal status. In this paper, the authors propose PSPRAY, a new kernel heap exploitation technique, which can significantly increase the reliability of the heap exploit against such a random mitigation technique.
Heap exploitations
In general, the memory corruption arising from the kernel heap area can be divided into three vulnerability types: out-of-bounds, use-after-free, and double-free.
- Out-Of-Bounds (OOB) is a vulnerability accessing beyond a predetermined heap object size. In order to exploit the OOB, an attacker should place two objects adjacently, a vulnerable object and a target object. Then the target object is overwritten by inducing a heap buffer overflow on the vulnerable object. In the random nature of SLUB allocator, the most common technique is Heap spraying. The attacker expects to allocate the vulnerable object right before the target object in coincidence.
- Use-After-Free (UAF) is a vulnerability if the object is accessed after being freed. To exploit UAF, an attacker needs to place the target object into the address, in which the vulnerable object was freed in advance. Then the attacker can corrupt the target object using the same virtual address of the vulnerable object. However, if CPU’s page is changed before allocating target object to designated virtual address, the attacker cannot place target object to the previous page’s address.
- The Double-Free (DF) vulnerability frees an object that has already been freed. In order to exploit the DF vulnerability, the attacker makes a dangling pointer in a way that a victim object is freed by the code of freeing the previous object being freed. Then, the attacker allocates the target object at the same address as victim object. However, this vulnerability has also the same limitation of UAF as well.
Pspray
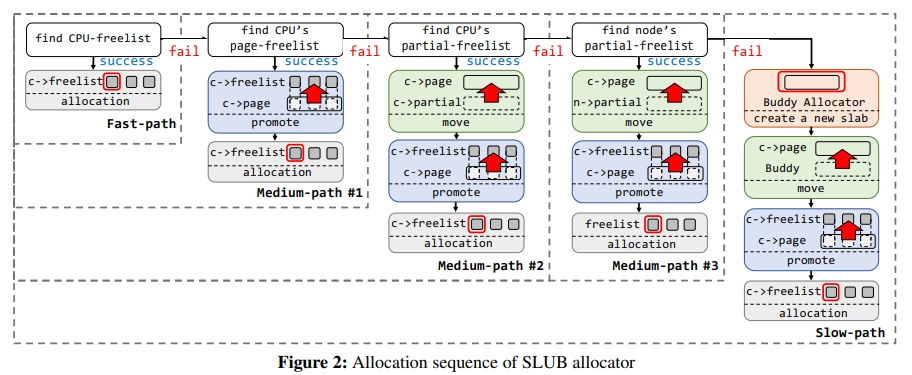
The major reason for exploitation failure is that the information about slab’s allocation status is not available to the attacker. There are 5 allocation paths in Slub allocation mechanism (fast-path, three medium paths, and slow-path). The behavior of the slow-path is unique from other paths. If the slow-path is taken, the kernel creates a new slab from the buddy allocator and allocates one object from the new slab. Therefore, using a timing side-channel attack, the allocation status of a new slab is predictable. PSPRAY is applied to exploit above-mentions vulnerabilities based on the observation.
Evaluation
The authors proved that slow-path can be intuitively distinguished through an experiment. Based on the feasibility, the authors conducted two extra experiments with PSPRAY on Ubuntu 18.04 LTS with Intel Xeon CPU @ 2.30GHz (48 cores) and 512GB RAM.

- In the first experiment conducted on isolated Linux VM for synthetic vulnerabilities of OOB, UAF, and DF, the results show that the average success rate of exploitation with PSPRAY is 94.61%, 100%, 100% on OOB, UAF, and DF, respectively, while the average success rate of exploitation without PSPRAY is 32.82%, 83.46%, and 83.67%, respectively. Moreover, the worst success rate of exploitation without PSPRAY is 17.94%, 51.46%, 50.59%, respectively, whereas PSPRAY has reliable success rates.

- In the second experiment for real-world exploitation to show the effect of noise on PSPRAY, idle state and busy state are simulated. Without PSPRAY, the success rate on average decreases as the workload becomes heavy (29.48%->22.19%, 66.56%->61.02%, 90.625%->88.64%). However, with PSPRAY, the success rate doesn’t decrease as many (95.29%->91.77%, 99.53%->98.96%, 99.99%->99.05%).
Mitigation
To mitigate timing side-channel based PSPRAY attack, the authors provide a solution to randomize the slow-path allocation, which is independent of the allocation status of freelist. The slow-path can be triggered at any point depending on how the freelist is randomized. The mitigation only modifies 13 LOC and the average overhead on performance and memory is around 1%. Finally, the overall success rate of using PSPRAY under the mitigations becomes similar to the success rate without PSPRAY.
Conclusion
The authors propose a new heap spraying technique that uses a timing side-channel, which can significantly increase the probability of an attacker’s exploit. Then, through synthetic and real-world vulnerabilities, PSPRAY demonstrates that it can circumvent the low exploitation success rates issue. Furthermore, they suggest a very simple but efficient mitigation technique for PSPRAY that successfully conceals when a new slab is used with negligible performance and memory overhead.
![[논문 리뷰] Pspray: Timing Side-Channel based Linux Kernel Heap Exploitation Technique](https://img1.daumcdn.net/thumb/R750x0/?scode=mtistory2&fname=https%3A%2F%2Fblog.kakaocdn.net%2Fdna%2FceVWRn%2FbtshbsyWHJX%2FAAAAAAAAAAAAAAAAAAAAAPpDDWfiwp5rkMtkVF9YJjJATZP5OzxPJlng8Fbh4T-r%2Fimg.png%3Fcredential%3DyqXZFxpELC7KVnFOS48ylbz2pIh7yKj8%26expires%3D1772290799%26allow_ip%3D%26allow_referer%3D%26signature%3DplkSW2b1JR43ZiYonC8h3rUXe4I%253D)