Authors:
Dmitry Kuznetsov and Adam Morrison, Tel Aviv University
Journal/Conference:
USENIX ATC 22'
Source:
https://www.usenix.org/conference/atc22/presentation/kuznetsov
Presentation material:
Abstract
System calls are the main method for applications to request services from the operating system, but their invocation incurs considerable overhead, which has been aggravated by mitigation mechanisms for transient execution attacks. Proposed approaches for reducing system call overhead all break the semantic equivalence between system calls and regular function calls (e.g., by making system calls asynchronous), and so their adoption requires rearchitecting applications.
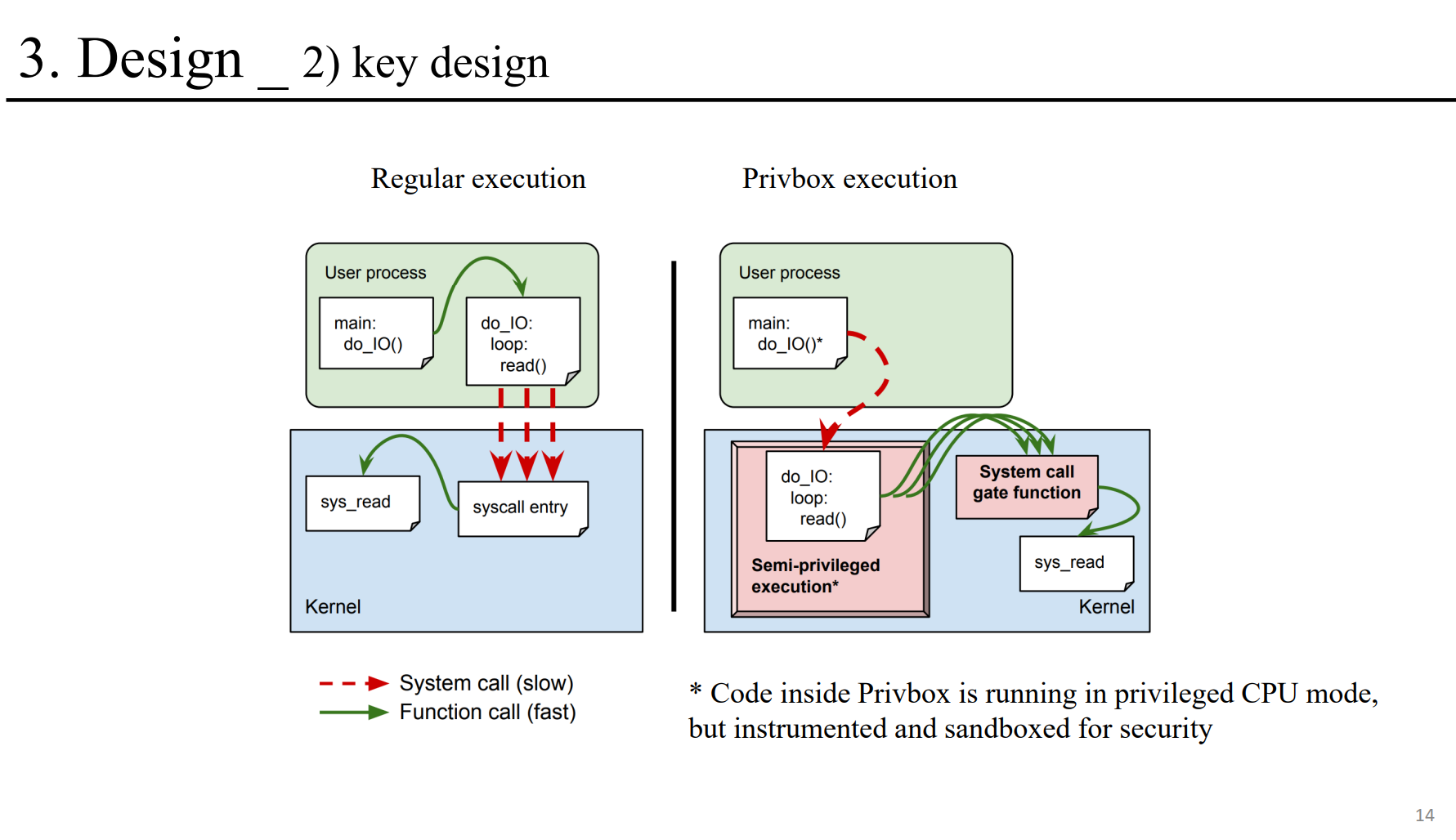
This paper proposes Privbox, a new approach for lightweight system calls that maintains the familiar synchronous, function-like system call model. Privbox allows an application to execute system call-intensive code in a \emph{semi-privileged, sandboxed} execution mode, called a 'privbox'. Semi-privileged execution is architecturally similar to the kernel's privileged execution, which enables faster invocation of system calls, but the code is sandboxed to ensure that it cannot use its elevated privileges to compromise the system.
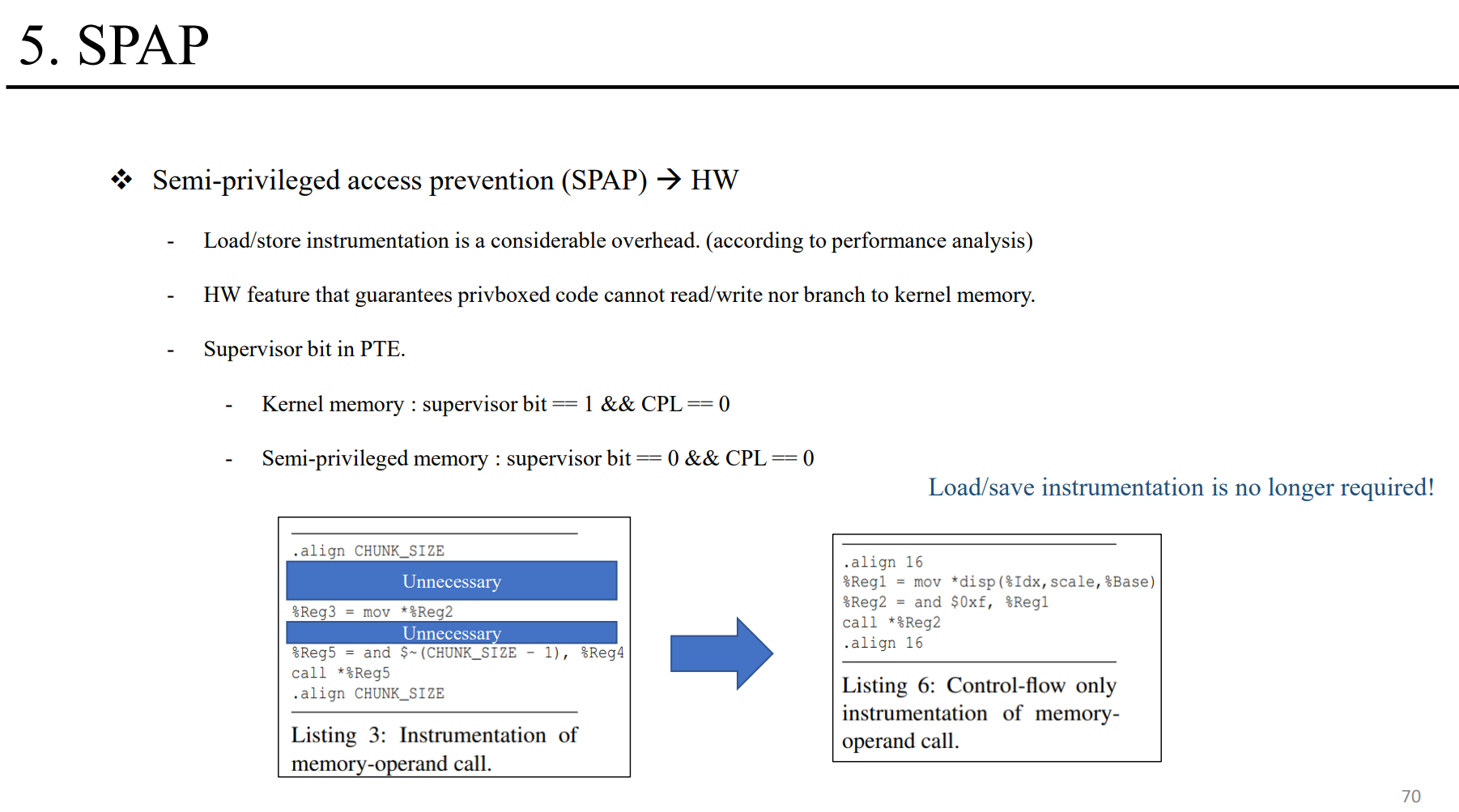
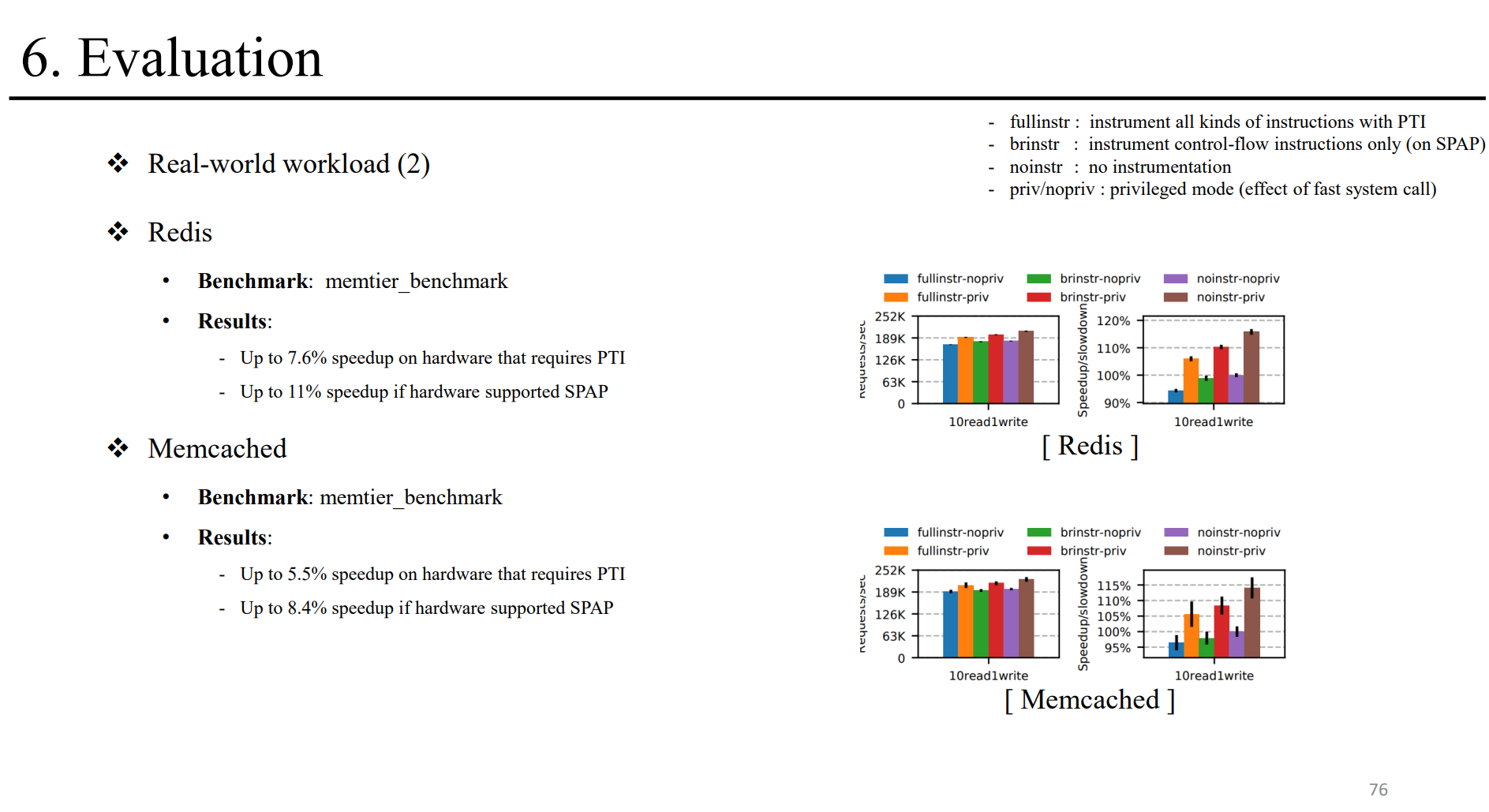
We further propose semi-privileged access prevention (SPAP), a simple hardware architectural feature that alleviates much of Privbox's instrumentation overhead. We implement Privbox based on Linux and LLVM. Our evaluation on x86 (Intel Skylake) hardware shows that Privbox (1) speeds up system call invocation by 2.2 times; (2) can increase throughput of I/O-threaded applications by up to 1.7 times; and (3) can increase the throughput of real-world workloads such as Redis by up to 7.6% and 11%, without and with SPAP, respectively.
Design

Implementation



HW optimization
Evaluation
Discussion

- How exactly does the Privbox manage custum page table? Usually a page table is allocated per one process.
![[논문 리뷰] Privbox: Faster System Calls Through Sandboxed Privileged Execution](https://img1.daumcdn.net/thumb/R750x0/?scode=mtistory2&fname=https%3A%2F%2Fblog.kakaocdn.net%2Fdna%2FoOTcF%2FbtshaUbpig9%2FAAAAAAAAAAAAAAAAAAAAAFGOtzcDj0UMkTiA-xdcri4mcrt40R5TDWiG_Wre7ZOg%2Fimg.png%3Fcredential%3DyqXZFxpELC7KVnFOS48ylbz2pIh7yKj8%26expires%3D1772290799%26allow_ip%3D%26allow_referer%3D%26signature%3D1Y0tS6%252FBWoxFDEfjJVEP8HYSqUw%253D)